Every now and then a new malware variant appears as a swift reminder that the security stakes are always rising. The QakBot/Pinkslipbot banking Trojan is one of them. The malware, not content with harvesting banking credentials, can now linger and act as a control server -- long after a security product stops its original purpose.
How does OakBot/Pinkslipbot remain active? And how can you completely remove it from your system?
QakBot/Pinkslipbot
This banking Trojan goes by two names: QakBot and Pinkslipbot. The malware itself isn't new. It was first deployed in the late 2000s, but is still causing issues over a decade later. Now, the Trojan has received an update that prolongs malicious activity, even if a security product curtails its original purpose.
The infection uses universal plug-and-play (UPnP) to open ports and allow incoming connections from anyone on the internet. Pinkslipbot is then used to harvest banking credentials. The usual array of malicious tools: keyloggers, password stealers, MITM browser attacks, digital certificate theft, FTP and POP3 credentials, and more. The malware controls a botnet estimated to contain over 500,000 computers. (What is a botnet, anyway?)
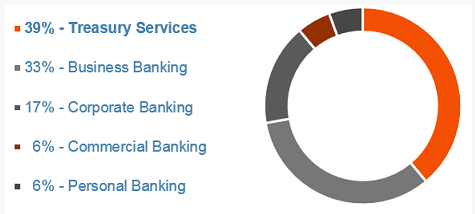
The malware predominantly focuses on the U.S. banking sector, with 89 percent of infected devices found in either treasury, corporate, or commerical banking facilities.
A New Variant
Researchers at McAfee Labs discovered the new Pinkslipbot variant.
"As UPnP assumes local applications and devices are trustworthy, it offers no security protections and is prone to abuse by any infected machine on the network. We have observed multiple Pinkslipbot control server proxies hosted on separate computers on the same home network as well as what appears to be a public Wi-Fi hotspot," says McAfee Anti-Malware Researcher Sanchit Karve. "As far as we know, Pinkslipbot is the first malware to use infected machines as HTTPS-based control servers and the second executable-based malware to use UPnP for port forwarding after the infamous Conficker worm in 2008."
Consequently, the McAfee research team (and others) are attempting to establish exactly how an infected machine becomes a proxy. Researchers believe three factors play a significant role:
- An IP address located in North America.
- A high-speed internet connection.
- The ability to open ports on an internet gateway using UPnP.
For instance, the malware downloads an image using Comcast'sSpeed Test service to double-check there is sufficient bandwidth available.
Once Pinkslipbot finds a suitable target machine, the malware issues a Simple Service Discovery Protocol packet to look for internet Gateway Devices (IGD). In turn, the IGD is checked for connectivity, with a positive result seeing the creation of port-forwarding rules.
As a result, once the malware author decides if a machine is suitable for infection, a Trojan binary downloads and deploys. This is responsible for the control server proxy communication.
Difficult to Obliterate
Even if your anti-virus or anti-malware suite has successfully detected and removed QakBot/Pinkslipbot, there is a chance it still serves as a control-server proxy for the malware. Your computer may well still be vulnerable, without you realizing.
"The port-forwarding rules created by Pinkslipbot are too generic to remove automatically without risking accidental network misconfigurations. And as most malware do not interfere with port-forwarding, anti-malware solutions may not revert such changes," says Karve. "Unfortunately, this means that your computer may still be vulnerable to outside attacks even if your antimalware product has successfully removed all Pinkslipbot binaries from your system."
The malware features worm-capabilites, which means it can self-replicate through shared network drives and other removable media. According to IBM X-Force researchers, it has caused Active Directory (AD) lockouts, forcing employees of affected banking organizations offline for hours at a time.
A Short Removal Guide
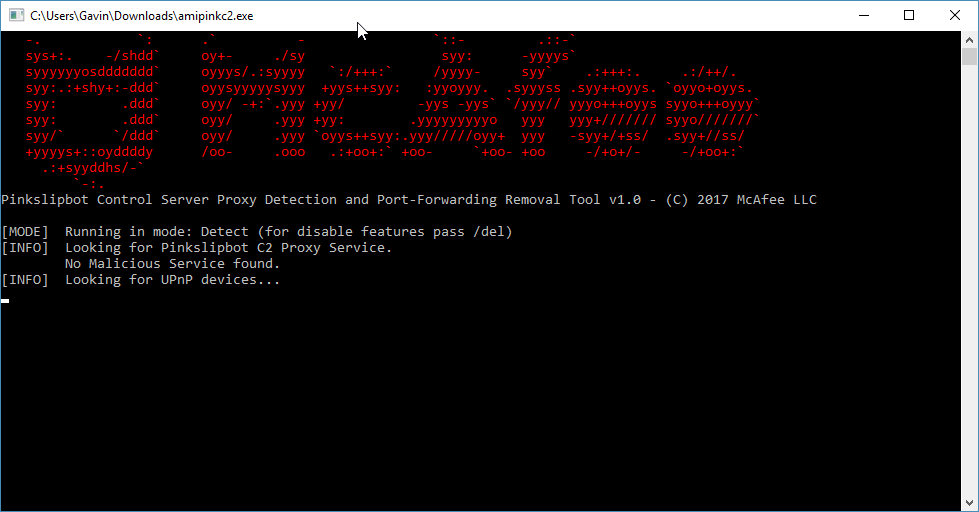
McAfee have released the Pinkslipbot Control Server Proxy Detection and Port-Forwarding Removal Tool (or PCSPDPFRT, for short... I'm joking). The tool is available for download right here. Furthermore, a short user manual is available here [PDF].
Once you've downloaded the tool, right-click and Run as administrator.
The tool automatically scans your system in "detect mode." If there is no malicious activity, the tool will automatically close without making any changes to your system or router configuration.
However, if the tool detects a malicious element, you can simply use the /del command to disable and remove the port-forwarding rules.
Avoiding Detection
It is somewhat suprising to see a banking Trojan of this sophistication.
Aside from the aforementioned Conficker worm "information about malicious use of UPnP by malware is scarce." More pertinently, it is a clear signal that IoT devices utilizing UPnP are a huge target (and vulnerability). As IoT devices become ubiquitous, you have to concede that cybercriminals have a golden opportunity. (Even your fridge is at risk!)
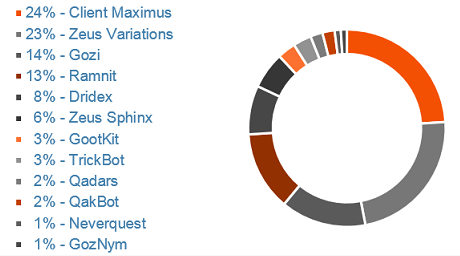
But while Pinkslipbot transitions into a difficult to remove malware variant, it is still only ranked #10 in the most prevalent financial malware types. The top spot is still held by Client Maximus.
Mitigation remains key to avoiding financial malware, be that business, enterprise, or home user. Basic education against phishing and other forms of targeted malicious activity go a massive way to stopping this type of infection entering an organization -- or even your home.
Affected by Pinkslipbot? Was it at home or your organization? Were you locked out of your system? Let us know your experiences below!
Image Credit: akocharm via Shutterstock